Black Hole
May contain traces of nut
Queueing decryption on HD-FOX, I'm getting Status = "FAILED", Log = "Plugin Failure".
The following lines appear relevant in auto.log:
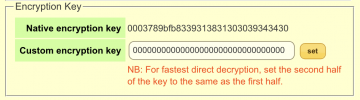
Settings shows this:
The following lines appear relevant in auto.log:
Code:
19/03/2021 22:03:02 - De-queuing 45 - decrypt - /media/drive1/Video/Star Trek_ Enterprise/Star Trek_ Enterprise_20210318_1900.ts
19/03/2021 22:03:03 - decrypt: DECRYPT: /media/drive1/Video/Star Trek_ Enterprise/Star Trek_ Enterprise_20210318_1900
19/03/2021 22:03:03 - decrypt: Direct decryption
19/03/2021 22:03:03 - decrypt:::decrypt::dequeue: /mod/etc/keys: No such file or directory
19/03/2021 22:03:03 - decrypt: /mod/webif/lib/ts.class:877 @
19/03/2021 22:03:03 - -1 - -
19/03/2021 22:03:03 - Plugin failure/mod/etc/keys: No such file or directory - what's that all about? Right enough, there's no such file or directory, but I'm sure I've done this before successfully.Settings shows this:

Last edited:

