graemev
New Member
I'm in the process of re-installing a Humax box and doing a Google search I came across at least two guys who have had the entire contents of the Humax indexed by google.
One of these (at least) has his box completely open , anybody could install or remove software from it (and indeed watch the programmes you recorded)
Now I could share their IP address here, but that would make them even more vulnerable to attack. So what I'll do is publish some screenshots of their recorded programmes. If you recognise these, then you should probably do something about it:
1: Add a password to your humax box
2: Consider changing your mapping of port 80 on modem to port 80 on Humax (e.g. map port 22080 to port 80 [don't use 22080 now I've mentioned it] This is only security through obscurity but I know from experience that it at least reduces the number of BotNets which try to brute force your password
3: Install a VPN
The 1st machine is called Foxsat-HDR and the recorded programmes look like:
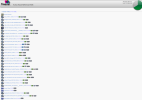
The second machine is called Foxsat-Left , and the contents are indexed (for all time?) by google, but currently port 80 is closed .... I could do a port-scan of his machine (since Google are highlighting it) but that seems a bit aggressive (so I won't) ..I believe, under EU law, you can ask google to "forget me"...not sure if we've also lost this protection.
One of these (at least) has his box completely open , anybody could install or remove software from it (and indeed watch the programmes you recorded)
Now I could share their IP address here, but that would make them even more vulnerable to attack. So what I'll do is publish some screenshots of their recorded programmes. If you recognise these, then you should probably do something about it:
1: Add a password to your humax box
2: Consider changing your mapping of port 80 on modem to port 80 on Humax (e.g. map port 22080 to port 80 [don't use 22080 now I've mentioned it] This is only security through obscurity but I know from experience that it at least reduces the number of BotNets which try to brute force your password
3: Install a VPN
The 1st machine is called Foxsat-HDR and the recorded programmes look like:

The second machine is called Foxsat-Left , and the contents are indexed (for all time?) by google, but currently port 80 is closed .... I could do a port-scan of his machine (since Google are highlighting it) but that seems a bit aggressive (so I won't) ..I believe, under EU law, you can ask google to "forget me"...not sure if we've also lost this protection.

