-
 The forum software that supports hummy.tv has been upgraded to XenForo 2.3!
The forum software that supports hummy.tv has been upgraded to XenForo 2.3!
Please bear with us as we continue to tweak things, and feel free to post any questions, issues or suggestions in the upgrade thread.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
WebIF - can it be accessed from the WAN?
- Thread starter makem
- Start date
Sam Widges
Active Member
Aha - that's SSL, not SSH.
As xyz321 says, install dropbear-ssh.
Edit- I see xyz321's beaten me to the reply
As xyz321 says, install dropbear-ssh.
Edit- I see xyz321's beaten me to the reply

Sam Widges
Active Member
Excellent - the next thing to do is to set up a port forward from your router on some random number to port 22 on the Humax. Then, point PuTTY at the router address and port and see if you can achieve the same.
Once that works, disable the port forwarding on the router and we'll work on making the config secure - the last thing that you want is for someone to find your SSH port and log in as root with the password humax!
Once that works, disable the port forwarding on the router and we'll work on making the config secure - the last thing that you want is for someone to find your SSH port and log in as root with the password humax!
makem
Member
Excellent - the next thing to do is to set up a port forward from your router on some random number to port 22 on the Humax. Then, point PuTTY at the router address and port and see if you can achieve the same.
Once that works, disable the port forwarding on the router and we'll work on making the config secure - the last thing that you want is for someone to find your SSH port and log in as root with the password humax!
Ok, will do that and thank again for your patience.
makem
Member
Logged in again on random port 
But can't access wibIF using http://127.0.0.1
Left the host name and port (22) as they were
Added a new tunnel127.0.0.1 with a new fwd port

But can't access wibIF using http://127.0.0.1
Left the host name and port (22) as they were
Added a new tunnel127.0.0.1 with a new fwd port
Sam Widges
Active Member
Don't worry, we're getting there.
Here are the instructions for the next stage (key updates highlighted):
Forward a TCP port on the outside of the router to port 22 on the Humax.
Open PuTTY and type the IP address of the Router into the "Host Name" box, make sure that the SSH radio button is selected - change the port number to the port number above.
In the LH window, open the config for Connection>SSH>Tunnels
In Source Port, type "80" and in Destination type "127.0.0.1:80". Make sure that the "Local" radiobutton is checked and then click on "Add"
Go back to "Session" in the LH window.
Type a name into the Saved Sessions window, e.g. "Routertest" and click on "Save"
Close any windows that are open to the target box, or just restart PuTTY to be really sure.
Double click on the Saved Session and you should get a login prompt - the default credentials are "root" and "humax"
If that works, then point a browser at http://127.0.0.1 and you should see the WebIF again.
Once it works, disable the port forward and we'll move onto the next step
Here are the instructions for the next stage (key updates highlighted):
Forward a TCP port on the outside of the router to port 22 on the Humax.
Open PuTTY and type the IP address of the Router into the "Host Name" box, make sure that the SSH radio button is selected - change the port number to the port number above.
In the LH window, open the config for Connection>SSH>Tunnels
In Source Port, type "80" and in Destination type "127.0.0.1:80". Make sure that the "Local" radiobutton is checked and then click on "Add"
Go back to "Session" in the LH window.
Type a name into the Saved Sessions window, e.g. "Routertest" and click on "Save"
Close any windows that are open to the target box, or just restart PuTTY to be really sure.
Double click on the Saved Session and you should get a login prompt - the default credentials are "root" and "humax"
If that works, then point a browser at http://127.0.0.1 and you should see the WebIF again.
Once it works, disable the port forward and we'll move onto the next step

Sam Widges
Active Member
Can we take 5 here for a moment? I've been working through some of the next stages with a view to writing them up and it's one of those situations where there is a bit of a steep learning curve and the steps are straightforward in hindsight but more difficult for the first-timer.
Before we go any further, could you have a think about what you want to achieve here and whether it would be simpler to just use the remote scheduler feature?
Alternatively, it may be better to revisit the use of SSL. I've not done it myself yet but I'd be willing to give it a punt.
Before we go any further, could you have a think about what you want to achieve here and whether it would be simpler to just use the remote scheduler feature?
Alternatively, it may be better to revisit the use of SSL. I've not done it myself yet but I'd be willing to give it a punt.
makem
Member
Yes, please do take 24hrs.
I want to connect in a secure manner from China, Malaysia and Singapore over the next 3 1/2 months to the humax.
I want to be able to download short tv programs and add one off recordings.
As I said earlier, I am well known in one particular city (local newspapers), in China where I will live with the locals for 3 weeks. As soon as it is known I am there I will be a target. The LAN from which I will be working is owned by my son in law who has many friends who have friends who have friends. I am sure they would find a way in. In the past I used his computer but never accessed home.
However If you think the work involved is too much to do for the reasons stated then lets drop it and the wife will have to do without her soaps.
I enjoy learning but it is too much to ask if it's is going to involve you in much work. I didn't think it would take so long (my fault)
I am grateful for the help so far, I have learned a lot. I think I should perhaps take a college course. It's a bit difficult due to travels tho.
I want to connect in a secure manner from China, Malaysia and Singapore over the next 3 1/2 months to the humax.
I want to be able to download short tv programs and add one off recordings.
As I said earlier, I am well known in one particular city (local newspapers), in China where I will live with the locals for 3 weeks. As soon as it is known I am there I will be a target. The LAN from which I will be working is owned by my son in law who has many friends who have friends who have friends. I am sure they would find a way in. In the past I used his computer but never accessed home.
However If you think the work involved is too much to do for the reasons stated then lets drop it and the wife will have to do without her soaps.
I enjoy learning but it is too much to ask if it's is going to involve you in much work. I didn't think it would take so long (my fault)
I am grateful for the help so far, I have learned a lot. I think I should perhaps take a college course. It's a bit difficult due to travels tho.
Sam Widges
Active Member
Makem,
I swapped some notes offline with af123 and he has very kindly added some tweaks to dropbear that should allow many of the next steps to be done through the web interface, which is definitely a case of going above and beyond the call of duty.
The next step that is needed is to create a key pair that you will be able to use to take the place of your password (I'll cover what that means later). I need to sort some stuff around the house, but could you have a look at the "PuTTYgen" utility and think of a good passphrase that you will use to secure your key. Think of something that is 10 or more characters long, has a mixture of uppercase and lowercase characters, as well as digits and punctuation. Steer clear of dates of birth and words from dictionaries as well, but whatever you do, make sure that you can remember it and not have to write it down.
I swapped some notes offline with af123 and he has very kindly added some tweaks to dropbear that should allow many of the next steps to be done through the web interface, which is definitely a case of going above and beyond the call of duty.
The next step that is needed is to create a key pair that you will be able to use to take the place of your password (I'll cover what that means later). I need to sort some stuff around the house, but could you have a look at the "PuTTYgen" utility and think of a good passphrase that you will use to secure your key. Think of something that is 10 or more characters long, has a mixture of uppercase and lowercase characters, as well as digits and punctuation. Steer clear of dates of birth and words from dictionaries as well, but whatever you do, make sure that you can remember it and not have to write it down.
makem
Member
Makem,
I swapped some notes offline with af123 and he has very kindly added some tweaks to dropbear that should allow many of the next steps to be done through the web interface, which is definitely a case of going above and beyond the call of duty.
The next step that is needed is to create a key pair that you will be able to use to take the place of your password (I'll cover what that means later). I need to sort some stuff around the house, but could you have a look at the "PuTTYgen" utility and think of a good passphrase that you will use to secure your key. Think of something that is 10 or more characters long, has a mixture of uppercase and lowercase characters, as well as digits and punctuation. Steer clear of dates of birth and words from dictionaries as well, but whatever you do, make sure that you can remember it and not have to write it down.
First, please thank af123 for me for going to such trouble on my behalf. Second, thank you for continuing. I hope that it will be of benefit to others as well as me to jusify your effort.
I know what a key pair means and how they are used. I have downloaded Puttygen and will investigate it's use having found a good guide. I understand the need for a good passphrase and what they comprise of.
Sam Widges
Active Member
As soon as af123 posts about the webif update on the announcements thread, I will be 'liking' it, and I hope that others do the same.
It's good that you know about key pairs, but others may not, so here goes...
In order to securely access your Humax from the outside using SSH, you need to find an alternative to the use of passwords and that is done using a pair of electronic keys. The keys are mathematically matched using a relationship that is easy for a computer to prove but is difficult to reconstruct if you only have one half. By 'difficult', I mean could it could take many many computers working full-time over decades and they still wouldn't crack it. The way that this works in practice is that one key is publicly used and the other is kept private and is passworded. To get access to the Humax, you save a copy of the public key on it and you keep the private key with you on a USB stick - when you want to log in to your box, you point PuTTY at the private key and it asks you for the password. If and only if everything works out, you get in.
So, how does that work in practice?
As we are using PuTTY in this example, this is what we will continue to use. There is a utility that comes with PuTTY called PuTTYgen and, if you have not got it already, then go to the website at http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html and download it.
Before you start, think of a good password - there is no point making use of heavy-duty cryptomathematics and then securing the private key with the passphrase 'letmein'. You will do everything to protect your private key, but if you do lose your USB stick, you need to make sure that you can sleep easy at night.
Run PuTTYgen and click the "Generate" button. Then waggle the mouse around in the window until the green bar reaches the end. When prompted, enter and confirm your passphrase.
Next, save the public and the private keys somewhere safe that you know is backed up but that nobody else has access to.
Then, select the text in the box marked "Public key for pasting into the OpenSSH Authorized keys file" and copy it.
There is a simple Youtube video on this part of the process which you can use to see the process in advance, here:
[Edit - that's fancy, I meant to just paste the link but it's been embedded, which is pretty neat  ]
]
Now, telnet or SSH into the Humax and run the following commands:
To test that this has worked, open PuTTY and edit the PuTTY session that you saved (see above) and go to Connection>SSH>Auth - in the box marked "Private Key File for Authentication", browse to the private key file that you generated with PuTTYgen.
Save the session and then open it.
You will be prompted for a username and then, instead of the password it will say "Authenticating with public key..." and ask you for the passphrase of the key. Type the password that you set above and hit return.
If all goes well, then you will have the usual "humax#" prompt.
If you don't get this prompt then don't worry because you can still telnet into the box to fix it. SSH will work as well, but you will need to temporarily delete the link to the key file so that you can go back to using password authentication.
Debugging - the 3 things that most often go wrong here are:
1) Incorrect access rights on /mod/.ssh (ls -al should show it as 'drwx------' Also, don't forget that the directory name has a '.' in front of it.
2) Incorrect access rights on /mod/.ssh/authorized_keys (ls -al should show it as 'rw-------') Also, don't forget the spelling - it's 'authorized' not 'authorised'.
3) Mistakes in pasting in the public key into the authorized_keys file - make sure that there is only one line and that there are no spaces in the long string of digits.
Once this has been sorted, we can move onto disabling passwords and accessing the Humax from the outside.
It's good that you know about key pairs, but others may not, so here goes...
In order to securely access your Humax from the outside using SSH, you need to find an alternative to the use of passwords and that is done using a pair of electronic keys. The keys are mathematically matched using a relationship that is easy for a computer to prove but is difficult to reconstruct if you only have one half. By 'difficult', I mean could it could take many many computers working full-time over decades and they still wouldn't crack it. The way that this works in practice is that one key is publicly used and the other is kept private and is passworded. To get access to the Humax, you save a copy of the public key on it and you keep the private key with you on a USB stick - when you want to log in to your box, you point PuTTY at the private key and it asks you for the password. If and only if everything works out, you get in.
So, how does that work in practice?
As we are using PuTTY in this example, this is what we will continue to use. There is a utility that comes with PuTTY called PuTTYgen and, if you have not got it already, then go to the website at http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html and download it.
Before you start, think of a good password - there is no point making use of heavy-duty cryptomathematics and then securing the private key with the passphrase 'letmein'. You will do everything to protect your private key, but if you do lose your USB stick, you need to make sure that you can sleep easy at night.
Run PuTTYgen and click the "Generate" button. Then waggle the mouse around in the window until the green bar reaches the end. When prompted, enter and confirm your passphrase.
Next, save the public and the private keys somewhere safe that you know is backed up but that nobody else has access to.
Then, select the text in the box marked "Public key for pasting into the OpenSSH Authorized keys file" and copy it.
There is a simple Youtube video on this part of the process which you can use to see the process in advance, here:
 ]
]Now, telnet or SSH into the Humax and run the following commands:
Code:
cd /mod
mkdir .ssh
chmod 700 .ssh
cd .ssh
echo "<paste your public key in here>" > authorized_keys
chmod 600 authorized_keysTo test that this has worked, open PuTTY and edit the PuTTY session that you saved (see above) and go to Connection>SSH>Auth - in the box marked "Private Key File for Authentication", browse to the private key file that you generated with PuTTYgen.
Save the session and then open it.
You will be prompted for a username and then, instead of the password it will say "Authenticating with public key..." and ask you for the passphrase of the key. Type the password that you set above and hit return.
If all goes well, then you will have the usual "humax#" prompt.
If you don't get this prompt then don't worry because you can still telnet into the box to fix it. SSH will work as well, but you will need to temporarily delete the link to the key file so that you can go back to using password authentication.
Debugging - the 3 things that most often go wrong here are:
1) Incorrect access rights on /mod/.ssh (ls -al should show it as 'drwx------' Also, don't forget that the directory name has a '.' in front of it.
2) Incorrect access rights on /mod/.ssh/authorized_keys (ls -al should show it as 'rw-------') Also, don't forget the spelling - it's 'authorized' not 'authorised'.
3) Mistakes in pasting in the public key into the authorized_keys file - make sure that there is only one line and that there are no spaces in the long string of digits.
Once this has been sorted, we can move onto disabling passwords and accessing the Humax from the outside.
I knocked up a quick diagram showing the set-up that you're aiming for - the Humax on the left and the remote PC/workstation from which you will access it on the right.
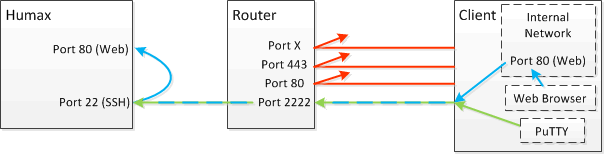
The only port that your router is going to let through is a high numbered random one (the diagram shows 2222 but anything that isn't a standard service port is good*. All other ports will be blocked on your router. If your router can support it, it will forward the request to the high numbered port on to the standard port 22 on the Humax. If not, the Humax can be made to present the SSH server on the same high numbered port you're using on the router.
You will connect to that high numbered port using PuTTY or some other SSH client, and you will configure the SSH client to create a tunnel for port 80 (standard web port) over the SSH connection. The SSH client will set up a dummy web server on the client machine that only listens on the local (loopback) address so it isn't accessible from other machines on the network, only from the client machine itself.
When you point a web browser at loopback (http://127.0.0.1/) then the SSH client multiplexes that traffic through the established secure SSH connection and when it gets to the other end then the traffic pops out and connects to the web server on the Humax. You see the Humax web interface in your browser.
* An attacker can still find the port if they're targetting your IP address but it will stop the people who just scan everything for the standard ports from prodding it every night)
HTH..

The only port that your router is going to let through is a high numbered random one (the diagram shows 2222 but anything that isn't a standard service port is good*. All other ports will be blocked on your router. If your router can support it, it will forward the request to the high numbered port on to the standard port 22 on the Humax. If not, the Humax can be made to present the SSH server on the same high numbered port you're using on the router.
You will connect to that high numbered port using PuTTY or some other SSH client, and you will configure the SSH client to create a tunnel for port 80 (standard web port) over the SSH connection. The SSH client will set up a dummy web server on the client machine that only listens on the local (loopback) address so it isn't accessible from other machines on the network, only from the client machine itself.
When you point a web browser at loopback (http://127.0.0.1/) then the SSH client multiplexes that traffic through the established secure SSH connection and when it gets to the other end then the traffic pops out and connects to the web server on the Humax. You see the Humax web interface in your browser.
* An attacker can still find the port if they're targetting your IP address but it will stop the people who just scan everything for the standard ports from prodding it every night)
HTH..
Sam Widges
Active Member
If it helps, tunnelling is like diplomats sending messages in the 'diplomatic bag' - the bag is the tunnel and port is the envelope with the address on the label.
makem
Member
Ok, made the keys, saved them. Ran the commands.
Didn't see any way to 'save' that session so closed the window and exited.
Edited the putty session, adding the private key. Saved it, and reopened.
Telnet back in and got the usual humax prompt.
Sorry about the changes - (too many interruptions)
Didn't see any way to 'save' that session so closed the window and exited.
Edited the putty session, adding the private key. Saved it, and reopened.
Telnet back in and got the usual humax prompt.
Sorry about the changes - (too many interruptions)
makem
Member
I think I should post the putty settings I have:
Session: 192.168.x.x port 23
SSH Auth: private key
Tunnels: L80 127.0.0.1::80
Local
Auto
Decided to try the settings we last used with the outside port:
Session: 192.168.x.x port 22
SSH Auth: private key
Tunnels: LXXXX 127.0.0.1:XXXX
Local
Auto
Get the Login as: prompt and request for password.
Session: 192.168.x.x port 23
SSH Auth: private key
Tunnels: L80 127.0.0.1::80
Local
Auto
Decided to try the settings we last used with the outside port:
Session: 192.168.x.x port 22
SSH Auth: private key
Tunnels: LXXXX 127.0.0.1:XXXX
Local
Auto
Get the Login as: prompt and request for password.
Sam Widges
Active Member
You're using telnet to port 23 - make sure that you are using SSH and that the port is 22.

